Protecting Applications
Companies need a way to protect their applications from piracy: TinyCLR OS running on SITCore boards gives you exactly what you need!
Debug Interface
In case you did not know, USB or serial ports are used to deploy applications. These interfaces can also be used to read the application. Sometimes we refer to the application as the deployment. All this is great for your own use, but what happens when someone wants to pirate your code?
Disabling the Interface
Thankfully, TinyCLR OS has an answer for that, and SITCore is designed with security in mind. The first thing you should do is disable the debug interface. This can be easily done with one line of code! This is stored in flash internally and will persist. The only way to undo this is by completely erasing the device using the bootloader.
GHIElectronics.TinyCLR.Update.Application.Lock()You can also check what interface is active , or if it is disabled.
GHIElectronics.TinyCLR.Native.DeviceInformation.DebugInterfaceApplication Deployment
Ok great! We have locked out anyone (including you and GHI Electronics) from accessing the application, but how can you update your device?! Not to worry, we have good answers for that as well.
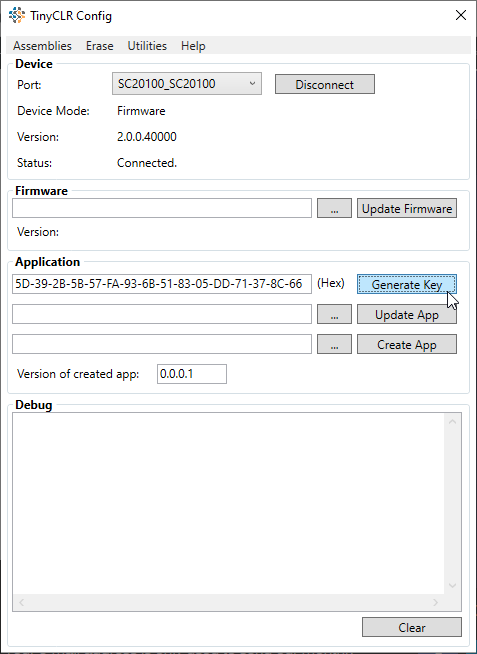
The first step is to create an encrypted copy of the application. This is easily done using the TinyCLR Config tool. You need to enter a key, or the tool will generate a key for you. The tool will then read the application, encrypt it, and store the encrypted application plus the key as files on your machine. Of course, this needs to be done before you disable the debug interface on your device!
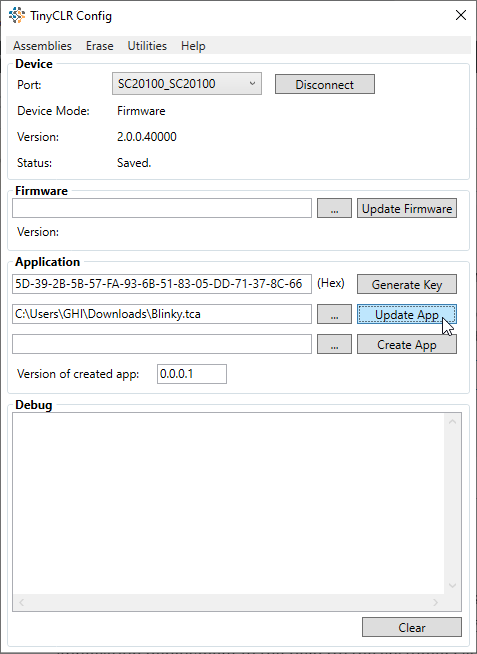
You can now use the application deployment to deploy to other devices. This is good for mass production BTW. Do not forget that you need the key if you are sending the deployment to a contract manufacturer.
In-Field Update
This is covered in detail in a different Tech Talk but in short, the application deployment can be loaded by your customer securely. You can send the application deployment to the field (to the customer) as a file in an email or automate it using the cloud. You have options. Of course, when you send the application deployment out to the field, you would not send the key with it. They key is securely stored inside your application, in your in-field update code.







Finally; application security.